Network Penetration Testing
SecureLayer7 performs known vulnerabilities test cases on target hosts, unlike traditional checklist execution. The video PoC is prepared to demonstrate a flaw in the network and understand its vulnerability.
We have provided the chronicle for client’s network security assessment methodology. During the time of assessment, the testing team will consider all latest vulnerabilities and security threats that were disclosed in the past 12 months & also look for any possible zero day disclosure(s).
Global standards and frameworks define the most efficient and effective methods to perform security assessments. They also differentiate and suggest assessment methodologies and processes based on the business requirements and the system architecture. Our security assessment methodology and process uses the following reliable open standards and frameworks.
What Securelayer7 offers

External Penetration Testing
Cybercriminals are continuingly looking for vulnerable servers or network devices on the internet. If the internet-facing asset is vulnerable for publicly available vulnerability, the attacker can gain access to the servers or network devices or system.

Internal Penetration Testing
Internal assets are most likely vulnerable to critical vulnerabilities. SecureLayer7 perform the pen test to identify such vulnerabilities and prepare to exploit for the found flaw and provide actionable mitigation.

Network Devices Penetration Testing
Certified penetration testers with years of experience perform manual penetration testing to seeks for security flaws in network devices.

Network Compliance Review
Security configuration audit makes your organization compliant with regulation such as SOC3, HIPAA, PCi-DSS, and others. SecureLayer7 helps you to fix security misconfigurations and identify non-compliant configurations to turn it into submissive.

Find our Cybersecurity Service reviews on Gartner
We have passion for securing Digital Businesses of our customers to make sure they are secure from critical vulnerabilities.
After using SL7 in a previous company, we contracted with them for Vulnerability Assessment for all of our various product lines, from consumer to enterprise. The results have been awesome
- Chief Security Architect in the Services IndustryIt offers incomparable accuracy since it is reinforced by unproved scanning and advanced network host correlation technology. The organizations are confident that their remediation exertions are closely focused.
- Cyber Security Consultant in the Services IndustrySecureLayer7's team went deep down into the rabbit hole to understand the product and find an issue with a business logic rule that took engineering several weeks to analyze within the code.
- Security Officer in the Healthcare IndustryOperations Insights from 2019
0+
Trusted Customers
Our customers from US, Middle East, India
0+
Delivered Hours
Annual Customer Pentest Hours
0K
Highest Ticket Size
From Enterprise Customer
0+
Retainer Customers
We belive serving best to all customers
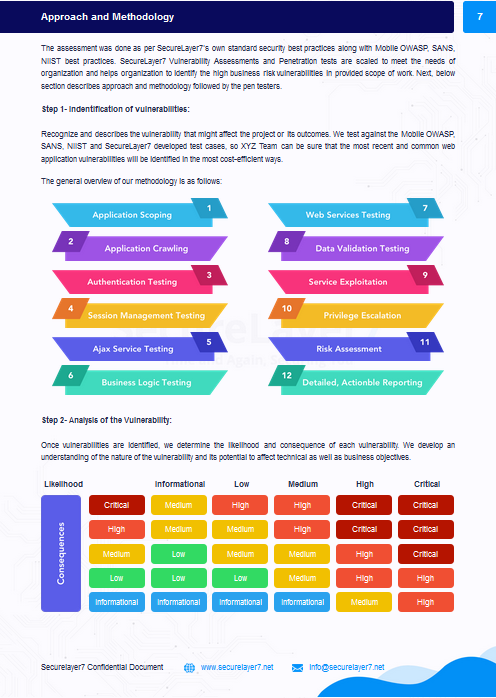
NETWORK SECURITY METHODOLOGY
SecureLayer7 perform in-depth enumeration on the targeted system to identify vulnerabilities and exploit them.
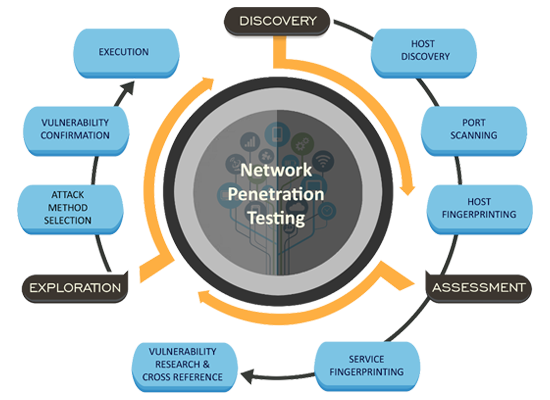
SecureLayer7 performs the network pen test based on years of experience and its ability to provide critical-to-low vulnerabilities in the network. SecureLayer7's team identifies vulnerabilities in the network assets using our network test cases, which are prepared from experience and standard NIST, OWASP, SANS, and OSSTMM guidelines.
First, perform the enumeration of a host IP address and identify different services on the host
Second, based on the attack surface found, we discover vulnerabilities in a host and exploit them further. The methodology includes first-host footprinting, live host detection, service enumeration, and operating system details. The exploitation process is an actual simulation, like cybercriminal exploitation, and using this method identifies multiple vulnerabilities.
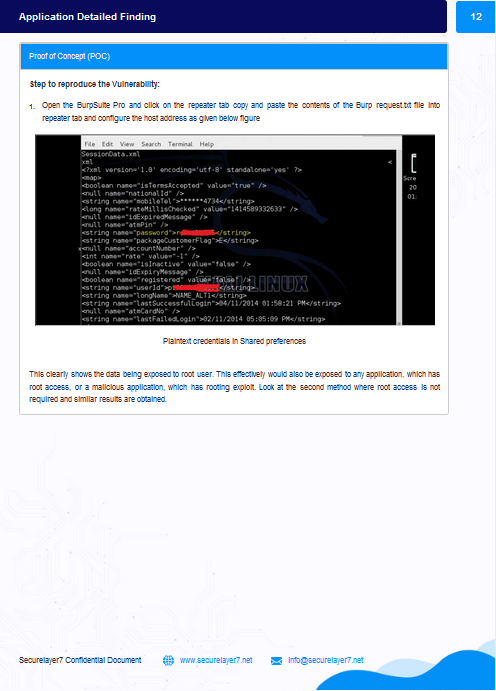
Using the identified vulnerability, exploit scripts will be prepared for exploitation along with video PoC, which demonstrates steps that re-create vulnerabilities.
Last, understand the risk of vulnerability and priority flaws according to the risk-rating matrix, and prepare a final report.
Network Security with Complete Coverage
WIRELESS PENETRATION TESTING
Wireless devices mostly use WPA2, WEP, and EAP authentication to the network. Recently, WPA2 was found vulnerable to KRACK (Key Reinstallation Attack); the WEP password can be easily guessed with network tools. SecureLayer7 looks for the potential vulnerabilities in the wireless network starting from the wireless LAN controller to the wireless devices.
HOST BUILD REVIEW
SecureLayer7 helps different organizations to secure the host OS environment. We review the host OS for the latest security patches and the best security implementations. This service helps the organization to maintain security and patching in the host OS environments.
NETWORK ARCHITECTURE REVIEW
Network Architecture Security Review. The objective of the network architecture security review is to identify weaknesses and gaps of existing security controls and to compare their alignment with the organization’s security objectives.

Securelayer7 regularly uncovers Zero Day vulnerabilities within a wide range of applications amidst research. We cooperatively work alongside vendors to catch up with the issues and disclose the needed prudently.
Take a look at SecureLayer7's Security Vulnerability publications and know more about the vulnerability disclosures, advisories, and reports. It details the security gaps identified in the web application, thick client software and also firmware’s of large enterprises. The documentation also contains the mitigation fixes for the vulnerabilities, their description, moreover the proof of concepts and security exposure information from SecureLayer7.
Research Presented at Conferences
SecureLayer7 deliverables
Securelayer7 website security solutions focus on the overall structure of your information and data management system. Client reports follow the same phillosophy and approch to prioritize useful deliverables in all client reports, including:
- Executive Summary
- Scope of the Work
- Approach and Methodology
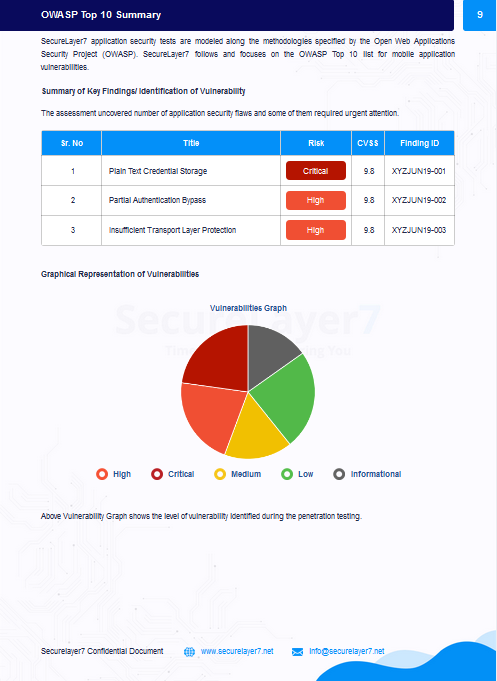
- OWASP Top 10 Summary
- Summary of Key Findings/ Identification of Vulnerability
- Graphical Representation of Vulnerabilities
- Summary of Recommendations
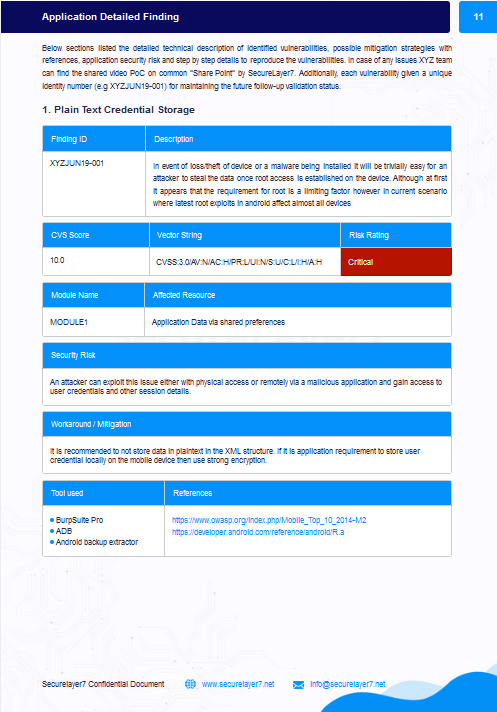
- Application Detailed Findings
- General Comments and Security Advice Conclusion
- Conclusion
Customer backed by
Advantages with SecureLayer7
Benefits of an Application penetration testing performed by SecureLayer7 include:
Meet Our Security Experts




About Securelayer7
SecureLayer7 is accredited with CERT-in and ISO 27001 certifications. CERT-in enables us to certify and perform security audits for Government agencies and BFSI customers. SecureLayer7 provides testing and reporting to support application security compliance against PCI, HIPAA, SOC type 1 and type 2, and other regulatory requirements. Customized scanning reporting templates that support internal standards and other regulatory requirements are covered by SecureLayer7.