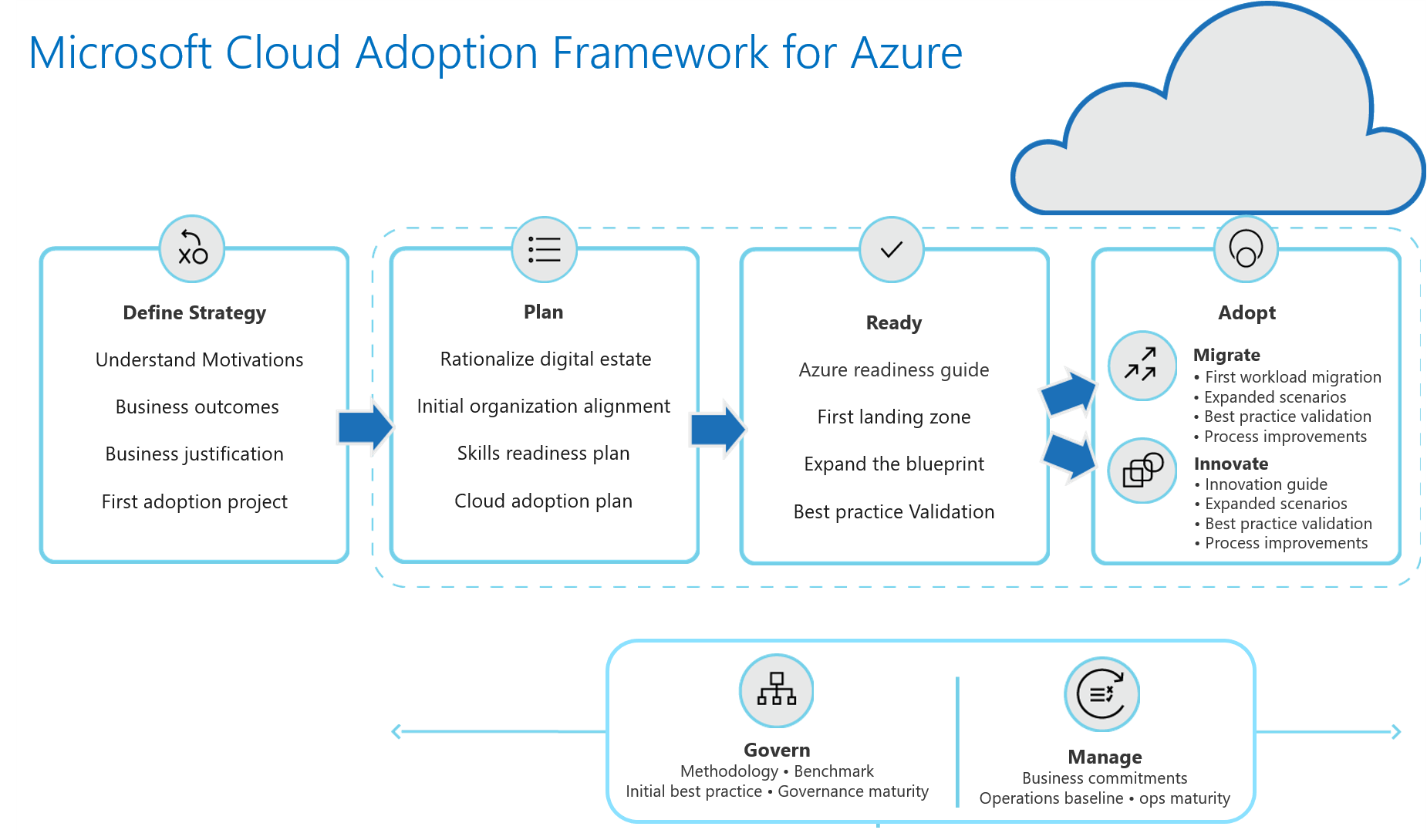
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s But the integration of new technologies brings about new security vulnerabilities as well. By penetration testing your Azure cloud environment, you can identify and eliminate these security risks – including those unique to your private cloud.
Microsoft Azure, like any other hosting and cloud platform, provides tradeoffs between control of resources and ease of implementation. Additionally, cybersecurity responsibilities are shared between you, the cloud customer, and Microsoft, the cloud-service provider. General hardening practices still apply, but the scale and customizability of the Azure platform gives you some tools in your security toolbox that may not be available in an on-premises data center. This blog post will walk through some of the available tools and provide insight into some of the tradeoffs you’ll have to make when deciding how to best secure your Azure cloud resources.