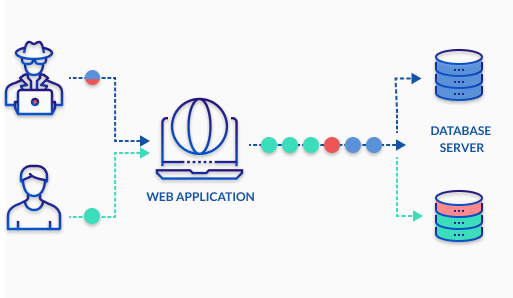
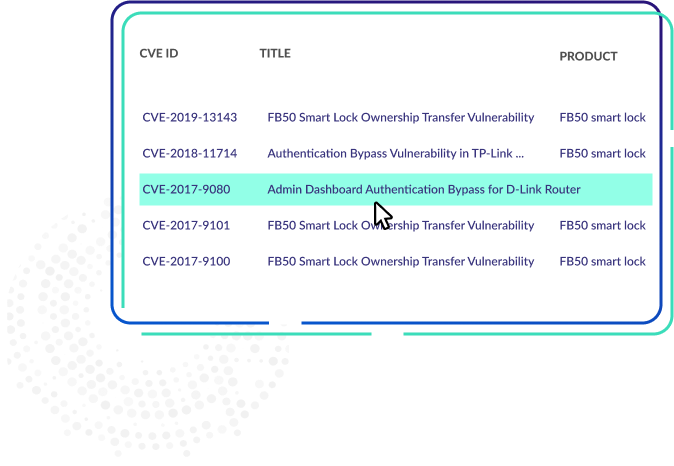
Thorough Insights
Identifying every detail that could be abused or find attack surfaces in the application. Insight of the application can be used to find critical vulnerabilities.

Vulnerabilites
Identifying the vulnerabilities in the application. Prioritizing high-risk vulnerabilities and providing a strategic plan to fix them.

Get Compliant
After performing patch verification, show customers, stakeholders your commitment towards security, and protecting important assets.