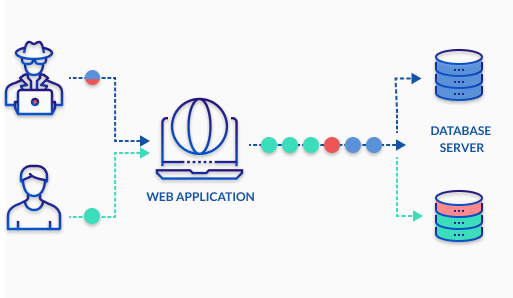
Thorough Insights
Identifying every detail that could be abused or find attack surfaces in the application. Insight of the application can be used to find critical vulnerabilities.

Business Logic Vulnerabilities
Detect and remedy any shortcomings in Business Logic that may create exploitable vulnerabilities in your applications.

Get Compliant
Get certified for GDPR, HIPAA, PCIDSS, ISO 27001 and SOC2 compliance through rigorous penetration tests.